Desktop:
C:\Users\*\Desktop\Outlook.lnk
Startmenu:
C:\Users\*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Outlook.lnk
Unfortunately, FSLogix isn’t able to hide application shortcuts that are located on redirected folders, so in case of folder redirection you can use WEM to manage the shortcut creation.
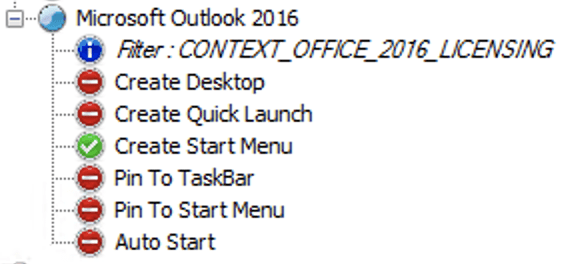
WEM is able to control the applications shortcuts which are created on the user desktop and/or start menu. First add an application, then assign this application to your users or better AD group. In this case it doesn’t matter if the folders are redirected or not.
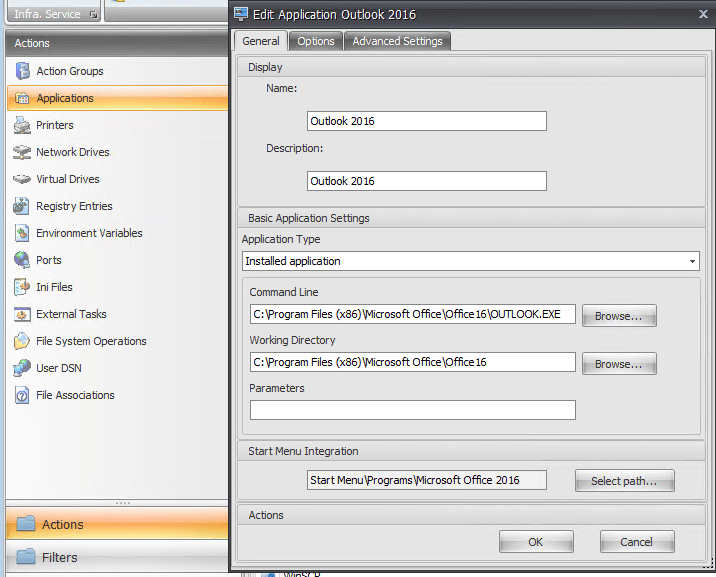
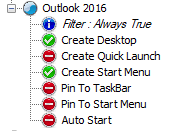
You should configure at least the following settings:
Computer Configuration – Administrative Templates – deviceTRUST
- Enable deviceTRUST (and supply a license, there are EVAL licenses available)
- Blacklist of users not controlled by deviceTRUST
- Whitelist of users not controlled by deviceTRUST
- All the Device properties you want to check and use for your context
Here you can find all the policy settings.
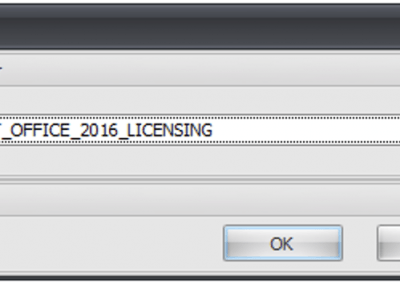
Let’s assume you want to check the device MAC address and the domain membership to make sure this is a “known” device for which you have a valid license.
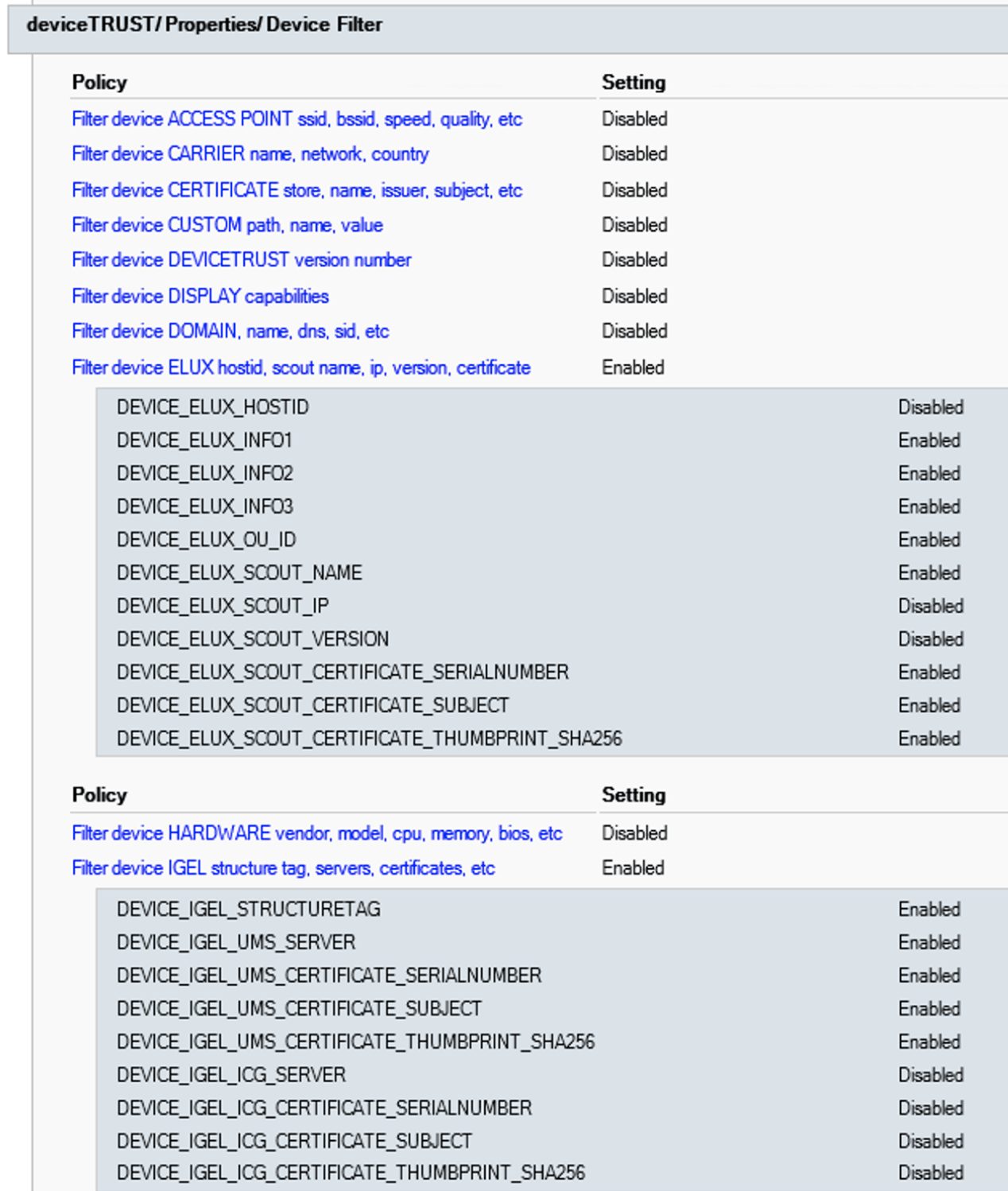
You have to configure the following device filters to get this information:
deviceTRUST/Properties/Device Filter
- Filter device DOMAIN, name, dns, sid, etc: DEVICE_DOMAIN_SID – Enabled
- device NETWORK ip, mac, dns, wifi, etc: DEVICE_NETWORK_X_MAC
Let’ see what information we get after a logon with a “deviceTRUST enabled” device which is a member of our domain. The content depends on what you have configured in the GPO:
Eventlog of VDA: (Applications and Services Logs\deviceTRUST\Admin):
Properties:
DEVICE_DOMAIN_DNS=domain.com
DEVICE_DOMAIN_SID=S-1-5-21-12345678910-987654321-1673703395
DEVICE_NAME=PC01
DEVICE_NETWORK_0_MAC=00-50-62-85-42-75
DEVICE_SCREENSAVER_ENABLED=false
DEVICE_SCREENSAVER_SECURE=false
DEVICE_SCREENSAVER_TIMEOUT=60
HOST_DEVICETRUST_CONNECTED=true
HOST_DEVICETRUST_VERSION=19.2.100.0
HOST_REMOTECONTROL_PROTOCOL=ICA
HOST_REMOTECONTROL_REMOTE_IP=172.26.1.21
HOST_REMOTECONTROL_REMOTE_PLATFORM=Windows
HOST_USER_NAME=testuer
MULTIHOP_COUNT=0
The same information is present in the following registry key of the VDA: HKEY_USERS\S-1-5-21-SID-OF-USER\SOFTWARE\deviceTRUST\Properties.
You can also get this information as environment variables.
Now we can use this information to create a “context” with deviceTRUST, to create a context you have to use the deviceTRUST Console which is integrated in GMPC. Open your deviceTRUST GPO and select deviceTRUST Console:
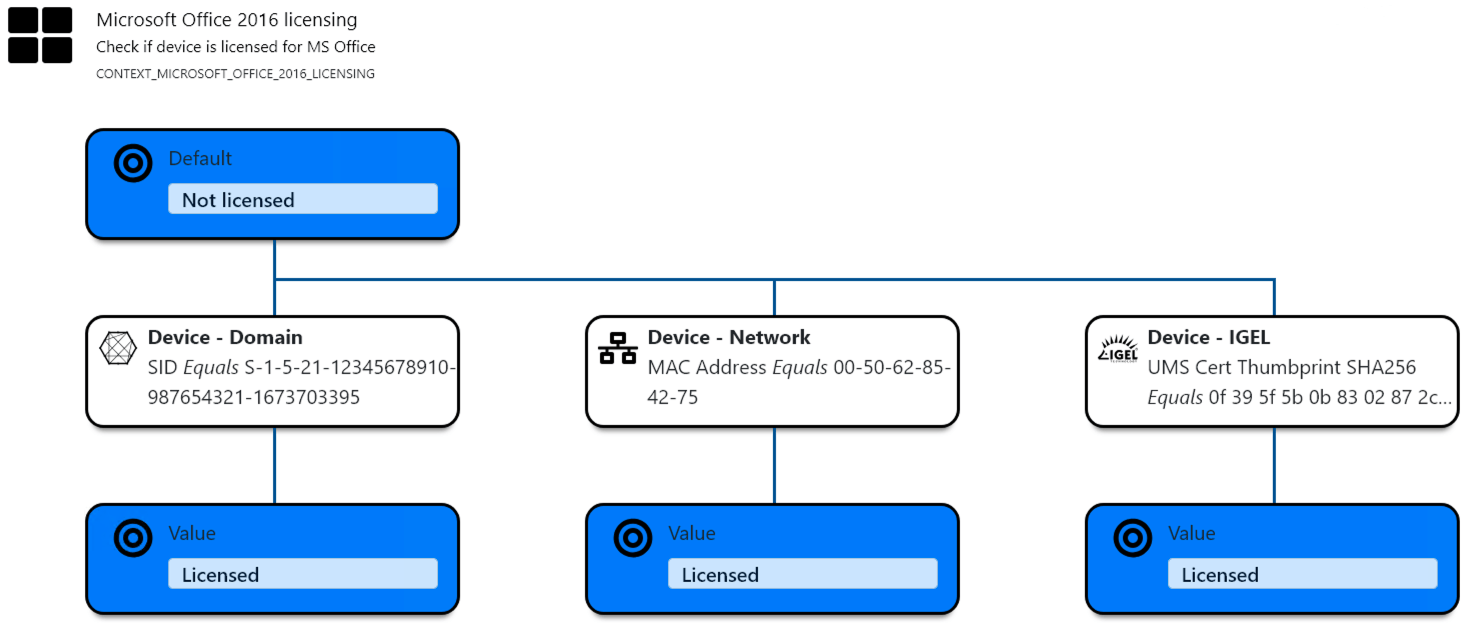
- Give your context a unique name
- Enter a description
- The Default value is “Not licensed”
- Check the domain SID (Windows) the MAC address and Igel UMS for example
- If it matches set the value to “Licensed”
- Give your action a unique name
- Enter a description
- Add a new trigger (context changed) and select the previously configured context with the value “Not licensed”
- Click next and select the filter “Logon”, click OK
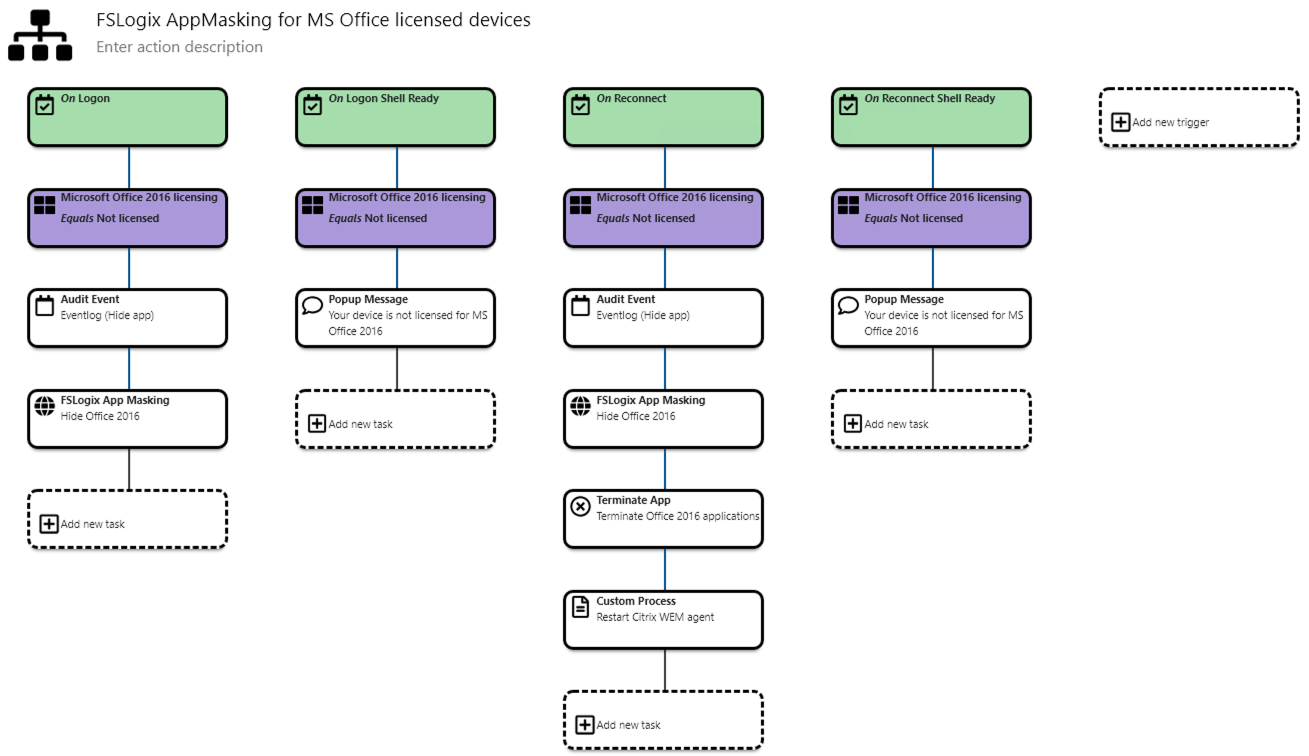
- Now you can add tasks like “Audit event”, “FSLogix AppMasking”, “Popup message”, etc.
- The last task should be “FSLogix AppMasking” to hide Office, cause the device is not licensed. It’s very simple, just enter the path of your AppMasking rule and select “Automatically revert to previous values on ‘Disconnect or Logoff’
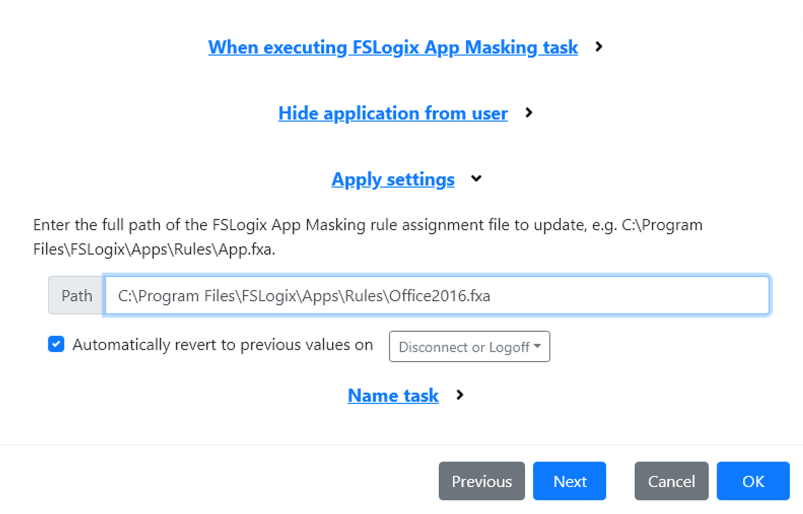
- Since we only want to take care of devices that are “Not licensed” we only have to create triggers for that condition.
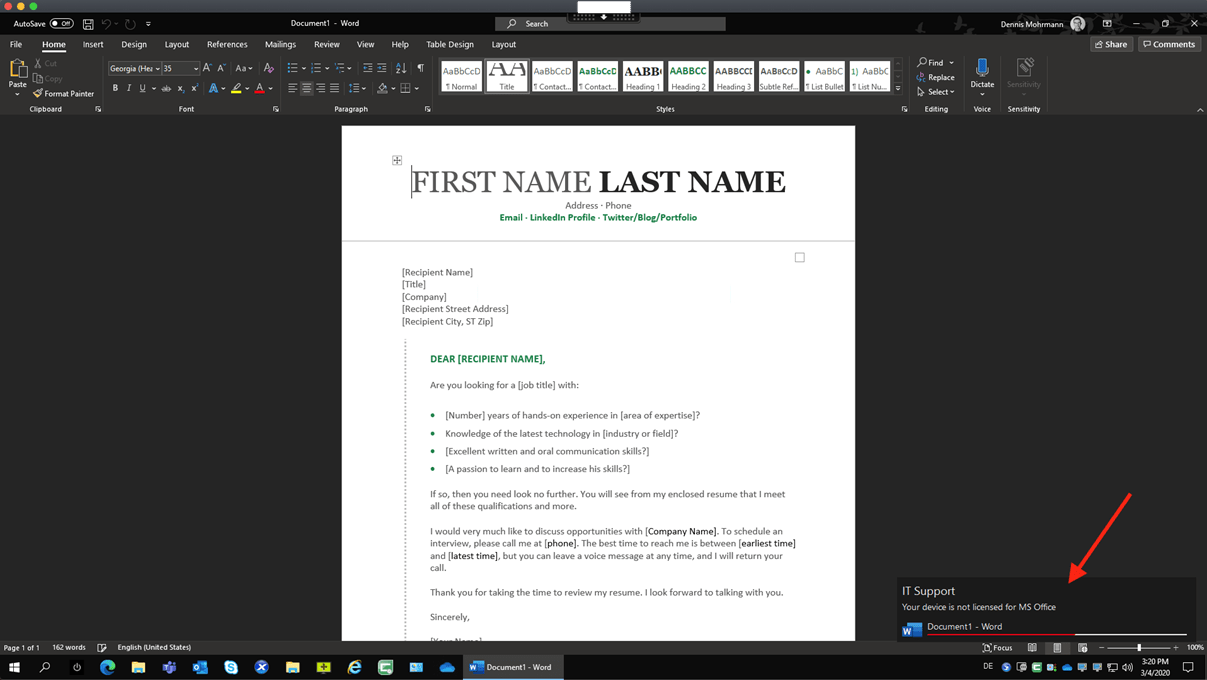
- If you want to inform the user that the device is not licensed for MS Office you can show a Popup message, but keep in mind that this requires a new trigger “On Logon Shell Ready” to make sure the shell is already loaded.
- If a user disconnects from a HDX session with a licensed corporate device and reconnects at home with a BYO device (which is not licensed) you have to use the “Reconnect” trigger and hide MS Office again with AppMasking. You can also terminate Office applications that the user left open while disconnecting
- Again, if you want to inform the user that the device is not licensed for MS Office you can show a Popup message, but keep in mind that this time you requires the trigger “On Reconnect Shell Ready” to make sure the shell is already loaded.
As already mentioned, if you use folder redirection for your user desktops you will realize that AppMasking isn’t able to hide the shortcuts on the desktop. Remember, we used WEM to create the shortcuts, so we have to change some configurations to deal with the creation and deletion of the shortcuts.
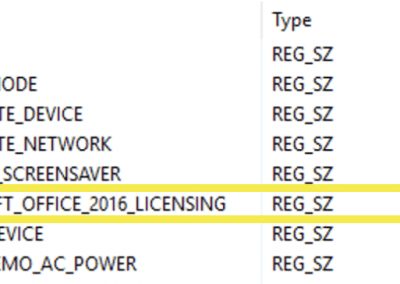
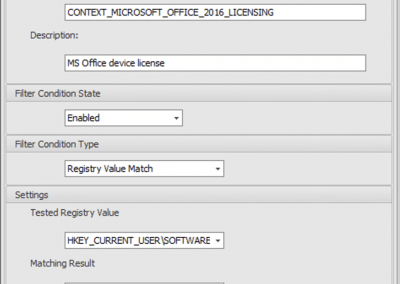
To tell WEM, that the app shortcut is only created when the device is licensed, we can use a filter. So, let’s create a condition to check a registry value from deviceTRUST and reassign the applications with WEM.
The context information for that is available in the registry under the key HKEY_CURRENT_USER\SOFTWARE\deviceTRUST\Contexts
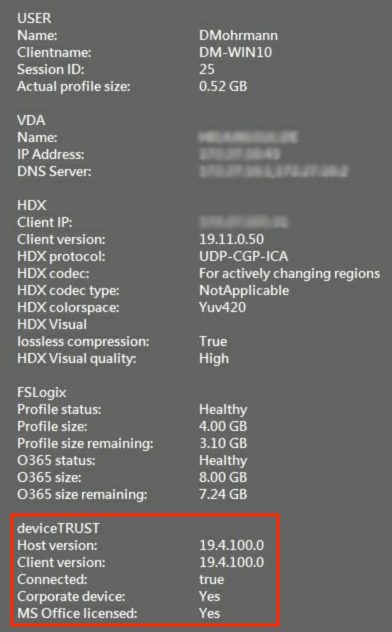
Corporate device connecting to VDA, deviceTRUST determines the context:

Eventlog:
User DOMAIN.DE\DMohrmann logged in.
Contexts:
CONTEXT_ACCESS_MODE=Internal-HDX
CONTEXT_CORPORATE_DEVICE=Yes
CONTEXT_MS_OFFICE_LICENSED=Yes
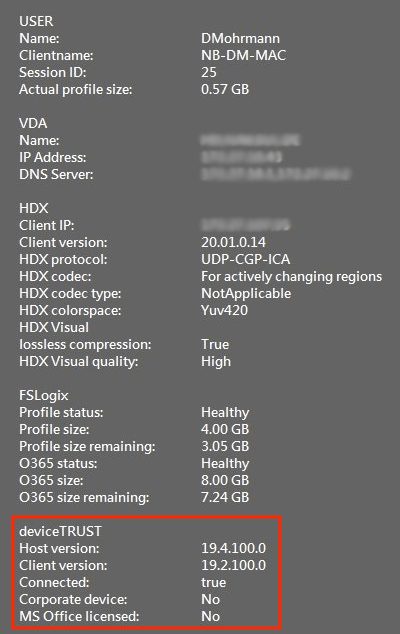
My customized BGInfo (Download here) reads this information from the registry:
This is how it looks like on a noncorporate device
Noncorporate device connecting to VDA, deviceTRUST determines the context:

Eventlog:
User DOMAIN.DE\DMohrmann logged in.
Contexts:
CONTEXT_ACCESS_MODE=Internal-HDX
CONTEXT_CORPORATE_DEVICE=No
CONTEXT_MS_OFFICE_LICENSED=No
Successfully updated App Masking rule assignment ‚C:\Program Files\FSLogix\Apps\Rules\Office.fxa‘ for user DOMAIN.DE\DMohrmann with operation ApplyUser.
My customized BGInfo (Download here) reads this information from the registry:
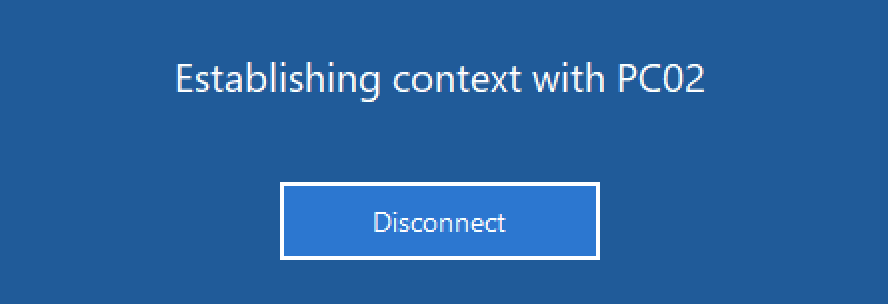
- User gets message after reconnecting (optional):
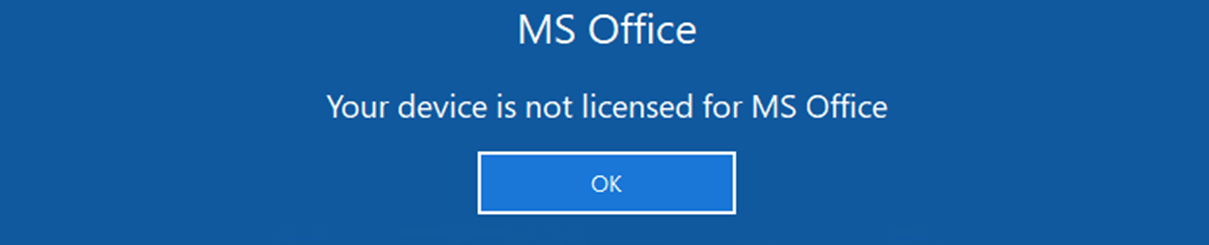
An event was generated for user DOMAIN.DE\dmohrmann.
Message: Microsoft Office isn’t licensed for user ‚dmohrmann‘ with the dem device ‚PC-02‘ (Context changed)
Successfully updated App Masking rule assignment ‚C:\Program Files\FSLogix\Apps\Rules\Office.fxa‘ for user DOMAIN.DE\dmohrmann with operation ApplyUser.
deviceTRUST triggers WEM agent to stop and restart, so that the shortcuts will be removed, otherwise they will become invalid
Office apps that are already open will be closed after a given time